TL;DR (but don’t stop here)
Most people burn time and money on certifications that don’t change their trajectory. Use this 4‑question framework every time you consider a cert:
Career Value: Does this tangibly move me toward the role I want?
Hands‑On Depth: Will I build and prove real skills, not just memorize trivia?
Planned Application: Exactly how (and how soon) will I use these skills on the job or in projects?
Faster Alternatives: Is there a more practical path (cert, lab, project) that gets me further, faster?
If the answer to any of these is weak, pass. Simple.
About Me
If you're new here, I'm Day, a Cybersecurity Engineer at Amazon. With five years in cybersecurity, my experience covers Detection Engineering, Cloud Security, Incident Response, Threat Hunting, and most recently, Threat Intelligence.
Before Amazon, I worked at Datadog as a cloud threat detection engineer, where I researched cloud threats and built detections for various cloud providers and SaaS applications.
I've worked my way up from various SOC analyst roles, investigating everything from endpoint threats to building detection systems for cloud-based abuse, so I know exactly what it takes to break into this field and make career advancements.
I started, just like many of you, learning from scratch, asking questions, and figuring it out one step at a time. And now, I'm here to help you do the same.
If you want to stay up-to-date on the cybersecurity industry and everything technical and career-related, be sure to like and subscribe to the newsletter for more content like this.
Join a vibrant cybersecurity community of over 6,800 people who are constantly engaging in conversations and supporting one another, covering topics from cybersecurity and college to certifications, resume assistance, and various non-professional interests like fitness, finance, anime, and other exciting subjects.
The Problem: Cert Chasing Without Strategy
I’ve taken numerous certifications for learning, career advancement, and as part of my time at WGU.
Some were worth it. Some weren’t.
The difference came down to one thing: did it create real leverage in my career?
2025 (or any year of your life) is not the time to spend on anything that doesn’t materially level you up.
No more paying for multiple‑choice trivia that never shows up in your day job.
No more “I’ll just add this to my résumé” without a plan to apply it.
Let’s fix the way you evaluate certs—once and for all.
The 4‑Question Certification Framework
1) Does it create career value?
Don’t start by asking “Is this cert popular?” Start by asking: “Does this push me directly toward the role, scope, or compensation band I’m targeting?”
How to test that quickly:
Pull 15–20 recent job postings for the role you want.
Highlight every required or “nice to have” cert. Notice the patterns.
Map the cert’s curriculum to the skills those jobs demand.
If there’s a weak or non‑existent connection, skip it.
If it doesn’t move you toward your target role, it’s a distraction.
2) Does it teach you hands‑on skills?
Multiple‑choice is not how modern teams validate your ability to ship, respond, detect, or break systems.
The market is flooded with practical training now. Use it.
Prefer these styles of exams and programs:
Hands‑on labs in real or simulated environments
Capstone projects that you can show and talk through
Scenario-based exams (IR, SOC triage, malware, adversary emulation)
Challenge platforms (HTB, TryHackMe, CyberDefenders) tied to certs
Examples:
Defensive / SOC:
Security Blue Team — BTL1
CyberDefenders — CCD
Hack The Box — CDSA
Offensive:
TCM — PNPT
INE/eLearnSecurity — eJPT, eCPPT, malware analysis tracks
Offensive Security — OSCP/OSEP (when you truly need that depth and rigor)
Cloud & AppSec:
Cloud Breach — Offensive AWS/Azure
Altered Security — Azure AD, Azure application security
Microsoft & AWS — now adding real lab credits so you actually deploy and test (you get Azure credit to build and break things + AWS Free Tier)
DevSecOps:
DevSecOps Institute and a growing set of hands‑on DevOps/SRE/Supply-chain security certs
If it’s not practical, you’re paying to forget it.
3) How will you apply it immediately?
If you don’t use it, you will lose it. Rapidly.
Before you pay:
Define the use case. “I’m an IR analyst who wants attacker empathy, so I’ll take PNPT and immediately emulate those TTPs to harden our detections.”
Define the artifact. “I will build a purple-team playbook, tune three detections, and push a Sigma rule PR by the end of the month.”
Define the repetition loop. “Every Friday, I’ll spend 90 minutes re‑running one offensive technique in the lab, documenting telemetry and defensive visibility gaps.”
No plan to apply = guaranteed skill decay.
4) Are there faster, more practical alternatives?
Many legacy certs still get promoted because they’ve been around forever. That doesn’t mean they’re the best for you.
Example: For the price of PenTest+, you can get PNPT, which gives you a complete end‑to‑end practical exam with reporting that mirrors real consulting work.
Same “destination” (penetration testing competency), but PNPT gets you there faster and deeper.
Ask yourself: Is there a practical training program, project, lab series, or community-driven cert that gets me to demonstrable skill faster?
If yes, choose that.
A Simple Scorecard (Use This Before You Swipe Your Card)
Score each question from 0 to 3. Anything <8 total is a pass for me.
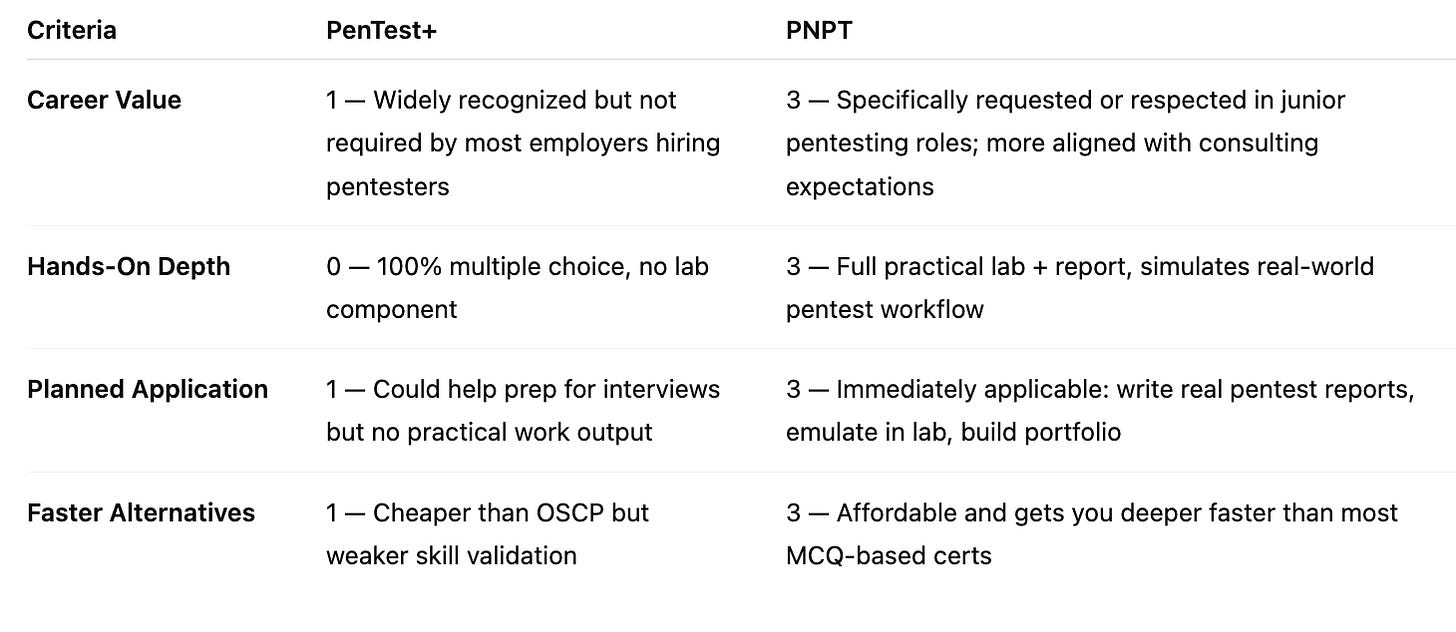
Sample Scorecard Evaluation: PenTest+ vs PNPT
🎯 Target Role: Junior Penetration Tester / Offensive Security Consultant
Total Score
PenTest+: 3/12 → ❌ Skip (Low value, not practical)
PNPT: 12/12 → ✅ Strong pick (Career-aligned, hands-on, and applicable)
Quick, Opinionated Shortlists
If you’re heading into SOC / IR / Detection Engineering
BTL1, CCD, CDSA, PJSA, SAL1
Practical Malware Analysis tracks (INE/eLearnSecurity)
Build Purple team labs (SCYTHE, Atomic Red Team, DetectionLab, etc.) + writeups
If you want Offensive Security / Adversary Emulation
PNPT (strong ROI)
CPTS, CJSA, PT1
eJPT → eCPPT progression
OSCP/OSEP when you need to clear that bar for specific roles or teams
If you’re focused on Cloud Security (Blue & Red)
Cloud Breach (AWS/Azure offensive)
Altered Security (Azure AD, Azure appsec)
Microsoft certs are now increasingly tied to real Azure credits and labs—use them in a practical way.
If you’re going DevSecOps / Platform Security / Supply Chain
Practical DevSecOps
Supplement with hands-on lab work: IaC scanning, SCA/SBOM pipelines, signing/verification, policy-as-code
Common Traps (Skip These)
Certs you can’t map to a role you actually want.
MCQ exams sold as “industry standard” with no lab component.
“I’ll just learn it now for later” with no maintenance plan.
Choosing the name-brand test when a practical, cheaper option exists.
Paying for prestige over proof. Hiring managers care far more about what you can do and show.
If You’re Still in School (WGU, bootcamps, etc.)
Use those required certs to build a practical foundation, then pivot hard into hands‑on paths:
Treat every “theory-heavy” cert as a primer, not the finish line.
Immediately wrap practical labs, projects, or purple-team exercises around the content.
Publish what you learn: detection writeups, IR playbooks, Sigma rules, Terraform modules, attack simulation notes… make it visible.
Action Plan (Do This Today)
Define your target role (title, team, and comp band).
Collect 15–20 job descriptions and extract the common required skills/tools.
List 3–5 certs you’re considering and run them through the scorecard.
Pick one that clears your bar.
Write a 4-week application plan: what you’ll build, tune, emulate, or publish using those skills.
Ship the artifact. Talk about it publicly (GitHub, blog, Substack, LinkedIn, X).
Rinse, refine, repeat.
My Final Take
Certifications can be either rocket fuel or busywork disguised as progress.
The difference is intentionality.
If it doesn’t add real value to your path, isn’t practical, won’t be applied, and has a better alternative, you already know the move: don’t take it.
Be surgical. Be practical.
Go further, faster, and smartly.
Cyberwox Resources
Resources for your career
🔹Join the Cyberwox Academy Discord!!
🔷 Check out the episodes of the Cyberstories Podcast on your favorite platform
🔹Cyberwox Cybersecurity Notion Templates for planning your career
🔹Cyberwox Best Entry-Level Cybersecurity Resume Template
🔹Learn AWS Threat Detection with my LinkedIn Learning Course
Closing
Once again, you made it this far :)
Feel free to reply, share your thoughts, or pass this on to someone who needs it.
Thanks for reading. If you'd like, you can subscribe and restack - it helps spread the word and encourages me to continue writing content. If not, I’ll see you around…somewhere on the internet!