HashiConf 2025 Recap - The Future of Cloud, AI, and Security
Expert insights from conversations around agentic infrastructure, GPU efficiency, and security that's actually shifting left.
Three days in San Francisco. Hundreds of engineers, architects, and builders. And one central theme: infrastructure is getting smarter.
HashiConf 2025 marked a turning point for how we think about automation, visibility, and security in the AI age. The announcements appear to be puzzle pieces forming a bigger vision of what HashiCorp plans for the future of infrastructure, which involves systems that understand context before they act.
From Project Infragraph to the rise of MCP-powered AI operations, every keynote, demo, and hallway conversation hinted at the same shift: the future of DevOps and cloud security is about orchestration backed by context.
This issue of Cyberwox Unplugged explores that future.
I already outlined the major releases and announcements in my vlog, so this newsletter will focus on practical insights from the field and discussions with key figures shaping the next phase, including HashiCorp’s leadership and practitioners working at a large scale.
Watch the full HashiConf 2025 vlog on the CYBERWOX YouTube channel for clips from these interviews and behind-the-scenes moments from San Francisco.
Standout Announcements
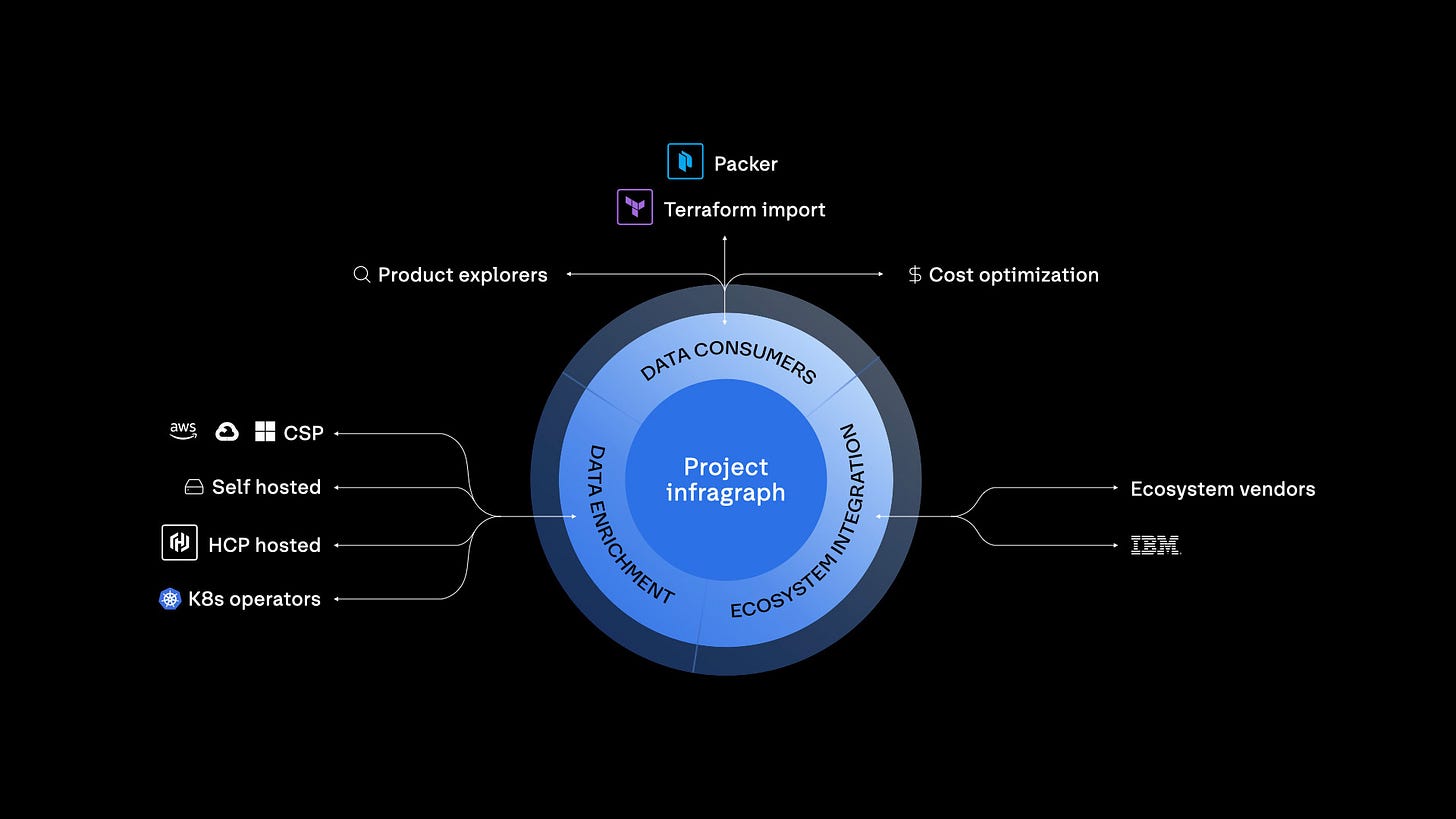
Project Infragraph offers a real-time, unified graph for managing multi-cloud and hybrid states. This feature is in private beta, expected in December 2025. Think of it as live topology and relationships that agentic systems can analyze.
MCP servers (Model Context Protocol) for Terraform, Vault, and HCP Vault Radar are now in public beta. They enable AI tools to securely initiate runs, read state, and execute common operations from an IDE or client. This serves as the link between current platforms and future agents.
Terraform gains more pragmatic power with Stacks GA, Actions for “Day 2” ops, and Terraform Search (long-requested) to discover unmanaged resources and bring them under IaC. Fewer click-ops, less drift.
Packer now offers SBOM storage (GA) and package visibility (beta) to mark images with provenance and software bills of materials, providing supply-chain transparency from the initial boot.
Vault & Radar updates enable secrets protection directly within your code editor, offering features like pre-commit detection, IDE workflows, and Jira SaaS scanning to ensure secrets are fixed before reaching the repository.
And so much more you can dive into below:
Expert Insights
Armon Dadgar on Simplifying Cloud Complexity
When I asked Armon Dadgar, Co-founder and CTO of HashiCorp, how he envisions helping organizations stay secure and operationally resilient as AI and multi-cloud adoption expand, his answer centered on three core themes:
standardization
managed delivery, and
AI-augmented visibility
“When we talk about our hybrid cloud operating model, it’s about how do you get to a standardized platform approach… Most enterprises are highly fragmented—they have a hundred app teams doing it a hundred different ways, and that’s an unmanageable level of complexity. You’re never going to get good at that, or be able to secure that.”
For Armon, security at scale begins with a unified platform strategy for provisioning, secrets management, and key management. Fragmentation, he noted, is the real enemy of operational maturity. The more unique patterns that emerge across teams, the harder it becomes to secure and automate them.
He went on to highlight a second primary focus: the HashiCorp Cloud Platform and the company’s broader managed services push.
“A lot of organizations lack the skills to actually deliver this stuff. So our big focus is: how do we run it as a managed service? We’ll handle integrations, backups, upgrades—all the stuff most teams struggle with.”
This reflects a long-term shift for HashiCorp from just being a tool provider to becoming a platform operator that helps enterprises consume secure infrastructure as a service, rather than a burden.
But Armon’s third point revealed where HashiCorp’s roadmap is truly heading: visibility and context through Project Infragraph.
“When I look at most outages or security issues, it’s not one system in isolation—it’s a chain of dependencies. The only way you solve that complexity is by visualizing it and seeing it.”
Infragraph, he explained, will help organizations map and understand relationships across their infrastructure, making cause-and-effect more visible across teams, clouds, and environments.
And once visibility is established, AI can play a significant operational role.
“Once you can visualize and see those relationships, that’s when AI augmentation starts making sense. You add MCP interfaces to something like Infragraph, and it starts unlocking day-two automation—the stuff we can’t really do today because the systems have no context.”
That last line says it all.
It doesn’t seem like HashiCorp is just chasing AI for the sake of hype. They seem to be building a contextual foundation that AI needs to operate responsibly in production systems, where visibility (from the context) is a fundamental requirement for AI autonomy.
Armon summed up the company’s mission clearly:
“Drive standardization, get to simplicity through a platform strategy, create consistent visibility, and ultimately help drive AI day-two operations.”
Will Bengtson on Platform Security and the Future of Infragraph
In our conversation, Will Bengtson, VP of Platform and Security Engineering at HashiCorp, gave a practical look into how HashiCorp runs its own products internally, as well as what excites him most about the company’s latest announcements.
“I own our cloud platform, HCP, and security… probably the most used tool for my teams is Terraform. Infrastructure as code lets us launch new features and deploy Infragraph with security baked in from the start.”
He also highlighted the critical role of Vault in their CI/CD processes and how it ties directly into HCP (HashiCorp Cloud Platform) — bringing secret management and compliance checks closer to the build pipeline. But when asked about his personal favorite tool, he didn’t hesitate:
“The one I love the most is Packer. Immutable infrastructure. Instead of patching, we just rebuild and redeploy. You can move infrastructure really fast.”
The mindset of rebuilding an image reflects a security engineer’s instinct to prefer known-good baselines over accumulated risk. It’s also the type of thinking that makes HashiCorp’s internal engineering culture mirror the ideals it advocates to its customers.
When we got into new announcements from HashiConf, Will pointed straight to Project Infragraph:
“The one I’m hearing the most buzz about is Infragraph. From a security perspective, asset management… from an ops perspective, being able to dig into a vulnerability, figure out where it lives in HCP or Packer, and trace it back into Terraform—that’s powerful.”
Seeing Infragraph’s first live demo alongside the rest of the audience, he noted that the natural language pre-built queries stood out the most:
“The pre-canned questions are super important—especially if you’ve never used it. You can filter and explore without needing to do everything manually. I thought the natural language hit hard.”
That’s the vision of Infragraph in action: making infrastructure and dependency visibility accessible not just to engineers but to anyone managing security and reliability at scale.
Before wrapping up, Will mentioned his next big “side project” — welcoming a new baby into the world. But even with that personal milestone ahead, his mind is already turning to what’s next for AI inside HashiCorp’s ecosystem:
“I’m really just trying to figure out where we’re going with AI next in our products. That’s going to be my new side project.”
All the best, Will!
Brian Chong on Scale, SBOMs, and the Next Layer of Infrastructure
Brian Chong, Director of Infrastructure and Security at Rubrik, brought a large-scale enterprise perspective to the table. His teams rely heavily on HashiCorp tooling—Terraform, Packer, and Vault—with an eye toward expanding into Nomad and Consul to extend automation beyond infrastructure and into service-level orchestration.
“Our three main tools are Terraform, Packer, and Vault. But we’re looking at Nomad and Consul as well.”
When asked which of the new announcements caught his attention, Brian didn’t hesitate:
“From my world, Terraform Actions. That’s going to help unify some of our toolsets and hopefully let me eliminate a few we already have. Optimization at our scale is always important.”
For him, the other standout was the new SBOM integration in Packer.
“As a security and compliance leader, SBOMs are a big deal. With the recent executive orders and all the discussion around supply-chain security, it’s good to see HashiCorp taking it seriously.”
He emphasized that the ability to automatically embed and track software bill of materials data directly within image metadata will streamline compliance workflows and help meet evolving regulatory requirements.
Looking ahead, Brian and his team are exploring Consul for service discovery and service mesh.
“We want to scale from infrastructure into the application tier. And integrating SBOM data into compliance systems will be a key next step.”
Rob Barnes on Nomad, Terraform Actions, and Building for the Ecosystem
In our conversation at HashiConf, Rob Barnes, Senior Developer Advocate at HashiCorp, shared a grounded perspective on Nomad’s flexibility, the future of Terraform, and what drives his work in connecting users to better workflows.
“Nomad is very underrated. It’s extremely flexible—which for me is one of its core strengths. It’s also extremely scalable… especially for high-performance workloads.”
Rob emphasized that while Nomad has long been seen as an alternative to Kubernetes, its scalability and simplicity make it an ideal choice for modern use cases, particularly in AI data centers, where speed and orchestration efficiency are critical.
When asked about the feature he’s most excited about from the conference, Rob didn’t hesitate:
“The clear winner is obviously Terraform Actions. Everyone’s super excited about that.”
He reflected on how Terraform Actions addresses a long-standing community desire for post-deployment operations—something many had tried to solve with Ansible-style provisioning. Rob admitted that HashiCorp’s earlier stance (“you have images, you don’t need provisioners”) made sense for its time, but “the world’s moved on.”
Now, Terraform Actions marks a major advancement in transforming Terraform from just a provisioning tool into a comprehensive lifecycle automation platform.
Beyond the announcements, Rob’s mindset as a developer advocate stood out. He talked about maintaining the Terraform provider “Terracurl”, which has surpassed two million downloads, and how the new features will soon impact his work directly.
“I can already see I’m going to start getting issues saying—‘Can you implement Terraform Actions?’ Once the conference season dies down, that’s probably what I’ll be working on.”
Outside of his conference workload, Rob’s also working on a five-part blog series on secrets consumption patterns (part 1 & part 2), exploring how organizations can better manage secrets at runtime across AWS Fargate and EC2 environments.
“I’m always looking at the problems people are facing and how, from an ecosystem perspective, we can build integration paths between where we are and where our users are.”
Tameika Reed on Accessibility, AI, and the Future of Infrastructure
Tameika Reed, founder of Women in Linux and infrastructure leader working across edge, cloud, and multi-cloud platforms, brought an energy to our conversation that cut straight to the heart of what HashiConf 2025 was all about.
“By day I lead a team of infrastructure and platform engineers building out edge nodes, cloud computing in multi-cloud environments, and securing those environments — on-prem, edge, and in the cloud.”
Her team’s toolkit reads like a HashiCorp product lineup: Boundary, Consul, Terraform, Vault, and even integrations with OpenShift, which she was particularly excited to see officially supported.
“I’m glad they integrated OpenShift with Vault — that was a big announcement.”
But what stood out most in our talk was how personal this evolution felt to her. Back in 2019, Tameika sat with Armon Dadgar in Amsterdam and shared a prediction:
“I said it’d be great to use AI on the backend of Terraform Cloud — to make suggestions based on what people have already deployed. To help them improve their infrastructure.”
Fast forward to 2025, and that idea has manifested as Terraform Search and MCP servers — both of which she views as major steps toward a more intelligent, guided DevOps experience.
“Here we are from 2019 to what we see now — Terraform Search, with import, and MCP servers that can make suggestions. If I’m a startup, I can use ChatGPT, Terraform Cloud, and MCP to spin up infrastructure really quickly — even without the budget for a full team yet.”
Tameika sees this not just as a technical improvement, but as an equalizer. For early-stage startups or small teams, these features bridge the gap between idea and implementation, allowing teams to deploy quickly, learn faster, and introduce governance later.
“Maybe I don’t have the money to maintain it just yet, but I can get up and running quickly. Then later, I can bring in someone to help maintain or govern it.”
When asked which announcements stood out to her most, she pointed to the same tools shaping the new AI-first operations model:
“I’m most excited about the MCP side and Terraform Search… Terraform Search helps people who already have infrastructure deployed — they don’t have to spend time importing it manually. It’s already there. Just import it, and you’re done.”
For Tameika, MCP is a sign of how AI is transforming how engineers learn and work
Tameika also raised an interesting question about the future of education and certification in this new AI-driven world.
“How does AI change exams? Are we going to be able to use AI on the exam when we’ve been using it all this time? Are we at the age now where exams don’t matter?”
It’s a fair question, honestly, and one that resonates across every industry where copilots and coding assistants are already part of daily workflows. If AI becomes the default partner in real-world engineering, traditional assessments might need to change to focus on judgment and design thinking, not just rote memorization.
Looking ahead, Tameika’s curiosity is far from slowing down. She’s currently studying Generative AI and security, exploring how tools like Vault, OpenShift, and MCP can converge into a secure, automated infrastructure workflow.
She’s also heading to KubeCon, where she expects to see how players like IBM, Red Hat, and HashiCorp might position themselves within the broader AI and quantum ecosystem.
“Just my personal opinion, but I think they’re looking to make a play with or alongside Palantir.”
And her long-term prediction feels both bold and inevitable:
“We’re going to reach a point where everyone’s just creating workflows. You’ll drag and drop what you want, it’ll generate the Terraform code for you, and you’ll hit run.”
That vision aligns perfectly with what’s already unfolding as infrastructure creation becomes more visual, collaborative, and accessible.
“No one cares that you know infrastructure as code. We just need to know: can you check it, does it work, and how much is it going to cost?”
Nasiullha Chaudhari on MCP Servers, AI, and Community Learning
Nasiullha Chaudhari, better known as Cloud Champ to his 160,000+ YouTube subscribers, joined HashiConf 2025 as both a HashiCorp Ambassador and a passionate community educator.
His content centers around cloud, DevOps, and automation, and that perspective showed clearly in our conversation.
“I use HashiCorp tools like Terraform, Waypoint, Boundary, and Consul. I’m here to learn more so I can use them better and share that knowledge with my community.”
When we talked about this year’s wave of announcements, Nasiullha didn’t hesitate to share his excitement centered around the new MCP Servers.
“Most importantly it’s going to be MCP Servers, because initially HashiCorp didn’t have an MCP server under their name. Now they do—for Terraform and other tools. I use Terraform the most, so I’m excited because with MCP, you can just tell the LLM in your language what you want, and it can do it for you.”
He described it as a major change in how people will create and control infrastructure, no longer relying on declarative files but instead using natural language instructions that generate Terraform configurations automatically.
“You can say, ‘I want to create infrastructure on AWS for my application,’ and it’ll do it without you writing the code. And since it’s good for production—you can even use modules and complex setups. I’m eager to test that out.”
But Nasiullha’s curiosity didn’t stop with MCP. He also spoke about Mitchell Hashimoto’s return and the reveal of The Story of Code project:
“I’m also excited to see what’s going on there and why Mitchell’s back. We saw the trailer, and it looked really interesting. With IBM now in the mix, I think we’re going to see even more exciting changes.”
That curiosity reflects what I’m also experiencing. I’m eager to see how HashiCorp’s new era under IBM unfolds with innovation while maintaining its open, developer-first spirit.
For Nasiullha, events like HashiConf are as much about connection as learning:
“These conferences give you exposure. They tell you what’s new, help you connect with other ambassadors and experts. I’m here to connect, learn, and grow.”
After the conference, his focus shifts right back to his audience:
“I’ll go back and start recording my videos again—it’s been long. I miss creating content. I also attend other conferences like KubeCon and DevOps events, but I’ll definitely be back for HashiConf 2026 in Atlanta.”
Takeaways
HashiConf 2025 was a mirror reflecting where the entire industry is heading.
Every conversation I had, from Armon Dadgar’s vision of agentic operations, to Will Bengtson’s emphasis on security baked into the platform, Rob Barnes’ focus on ecosystem enablement, Tameika Reed’s push for developer accessibility through AI, Brian Chong’s enterprise lens on SBOMs and compliance, and Nasiullha Chaudhari’s community perspective, pointed toward the same reality:
The next era of cloud and security won’t be built by humans or machines. It’ll be built with them.
Infrastructure now needs to become more contextual because the tooling is shifting from things we configure to technological partners (AI) that we guide, systems that reason about their environment (AI), operate safely within policy (AI), and adapt as quickly as the organizations behind them (even more AI).
Automation appears to be evolving beyond infrastructure efficiency but more towards infrastructure resilience, backed by the aforementioned context.
And visibility, like the kind HashiCorp is now enabling through Infragraph, is evolving beyond dashboards and charts to bridge the trust gap between people, processes, and the AI that will soon help operate them.
As builders, our role must evolve from writing code that simply executes to designing & architecting resilient systems at scale.
A huge thank you to HashiCorp for sponsoring my trip to San Francisco for HashiConf 2025 and giving me the chance to meet so many brilliant builders and security minds in person.
This newsletter, however, isn’t sponsored by them. It’s an independent reflection written from my own experience, perspective, and conversations throughout the event.









